migRaven.Analyzer
Reporting on the actual status of your data and authorization structure
The new migRaven.Analyzer gives you full insight into the structure of the data and access rights to the file server and AD.
How safe and efficient is your data storage?
In times of big data and seemingly unlimited disk space, concepts to clean up file services are becoming a rarity. This is a mistake, because data does not only occupy space on the server: Your company's data is above all else - they are an essential and valuable tool for your employees. The smooth, simple and safe handling of this ever-growing data mountain therefore holds great potential: migRaven.Analyzer visualized and evaluated the usability of your data and thus the efficiency of all users in dealing with file storage.
Your company's data is an essential and valuable tool for your employees
For this purpose, all information about file services, data structures, access rights and AD objects is merged. On the basis of current best practice specifications and many years of experience, the actual state of your data storage is evaluated in terms of efficiency and safety and made comprehensible in meaningful representations.
migRaven.Analyzer in the webinar on Monday, 29. January at 14: 30 clock
>> Check out now! (Part 2/4)
Obsolete Data Report
At the beginning of each optimization is the analysis of the actual state: This migRaven.one report therefore shows you quickly and clearly what is difficult to do with Windows on-board resources: Where in directories have deposited large amounts of data and how old this or the they are containing structure. In doing so, you set yourself from which period data should be considered obsolete or at least outdated and then see how many of the existing directories and files on a share applies or how large the occupied space of these files in total. In addition, these values are presented in relation to the total amount of data - often with the result that 70% and more of the data could have been archived or deleted long ago.
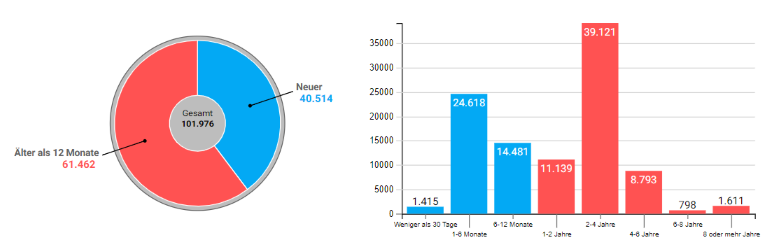
Thanks to the Obsolete Data Report, you can purposefully take action against these mountains of data and thus increase the efficiency of all users in handling the file system.
Active Directory visualization & statistics
The AD statistics first give you a quantitative overview of the existing accounts and groups in all imported ADs. See at a glance whether the number of users and computer accounts and the security groups used are correct. In addition, migRaven.Analyzer lets you comfortably browse through your AD objects in order to understand the complex relationships, memberships and relationships between the user accounts and the authorization groups. In this way, information can be obtained in a targeted and clear manner if there are questions about the authorizations of individual users or groups.
Best Practice Report
The best practice report provides detailed key figures relating to the Microsoft best practice compliance of your authorizations on the read drive. Easily find out where, for example, authorizations are too deep, inheritance is interrupted or users are directly authorized. This information is indispensable when preparing for a file server restructuring or when cleaning up the Active Directory.
-
Permission levels
In order to make the administration of authorizations as easy as possible, permissions should not be set too low. In doing so, level 3 of the directory structure has proven to be optimal directory depth. Because every explicit right below level 1 makes it necessary that list permissions are also set up so that the user can even get to the actual directory. The migRaven.one report shows you in detail how low your permissions are in your environment and the resulting average level of privilege.
-
Inheritance interruption
The interruption of inheritances should be avoided just like Deny permissions. Even though it may seem reasonable in certain situations, this procedure provokes additional effort in the further lifecycle of the system, for example when it becomes necessary to pass on authorizations. The report shows you all interrupted inheritances. It is recommended to work according to the Least Privilege Principle: always only allocate as many authorizations as are actually needed. This necessitates a change of view when assigning permissions. You do not set rights from above but from below. This means that, for example, at the level above an explicitly assigned Modify right, only list permissions are required for this to work.
-
Directly entitled persons
Another recommendation is the use of groups for authorization. Groups make it possible to assign rights for many users. Because ACLs are basically limited and there are easy performance issues if there are too many ACEs. The report shows how many users are directly authorized in an environment that is not an administrator. After best practice one should work according to the principle AG-DL (or G, or U) -P: The account comes into a role group (G), this into authorization groups (DL) - this in turn becomes a member of the P (ACL). However, it makes sense to dispense with the role group in certain cases, eg if the user combination is only needed for a single directory. Exactly then one uses A - () - DL-P - the users become the direct member in the authorization group. This ensures that no users are authorized directly in an ACL.
-
Orphaned ACE
Orphan ACEs occur when an account is deleted from the AD without removing the ACE entries. This is not a technical problem but a "blemish", which of course also affects the reporting.


